Transition statement NSCIB - EUCC
This memo serves as clarification and guidance to the IT-product cybersecurity certification market players regarding the transition from the Netherlands Scheme for Certification in the Area of IT Security (NSCIB) to the European Common Criteria-based Cybersecurity Certification Scheme (EUCC) in the Netherlands.
This is a shared memo by the Dutch Authority for Digital Infrastructure (Dutch: Rijksinspectie Digitale Infrastructuur, RDI) in its role as the Dutch National Cybersecurity Certification Authority (NCCA) and the General Intelligence and Security Service (Dutch: Algemene Inlichtingen- en Veiligheidsdienst, AIVD), who are the authorising governmental bodies for the EUCC scheme in the Netherlands and the NSCIB scheme respectively.
Transition timeline and clarification
Relevant dates from the EUCC Implementing Regulation are:
- 27 February 2024 – Entry into force, start of accreditation & authorisation of CABS and EUCC applications;
- 27 February 2025 – All articles fully apply, and EUCC certificates can be issued;
- 27 February 2026 – National CC schemes cease to produce effects.
The Netherlands’ intention is to motivate ITSEFs and CBs to obtain their EUCC licensing status as soon as possible and to encourage sponsors to start their Common Criteria projects under EUCC. To support this, EUCC projects will be prioritised over NSCIB projects in our combined internal resource planning. This may lead to longer timelines for NSCIB projects.
To clarify the transition from NSCIB to EUCC, the following timeline has been created, with added explanation to each stage of transition:
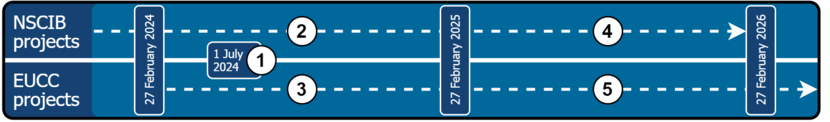
- In accordance with the CC2022 transition policy as published on the CCRA website:
- All initial certification projects starting from 1 July 2024 shall use the CC2022 version of the Common Criteria standard. In anticipation of this deadline, NSCIB will start accepting applications using the new version of the standard effective immediately.
- CCv3.1 assurance continuity re-certification projects (re-evaluation, and re-assessment) can be requested for up to 2 years after the initial certification date under both NSCIB and EUCC. To determine whether to start a CCv3.1 assurance continuity project under NSCIB or EUCC, consult the NSCIB - EUCC transition restrictions described in the points below.
- NSCIB will only accept certification applications (including re-certification applications) between 27 February 2024 and 27 February 2025 through current licensed NSCIB bodies if the following conditions are met:
- The ITSEF and CB are not yet licensed for EUCC. If the ITSEF and CB are licensed for EUCC and want to run a NSCIB project, argumentation to the need of an NSCIB certificate is required. The decision on granting this will remain at the discretion of the NSCIB scheme;
- The assessment plan is approved before 27 February 2025;
- The project has a realistic timeline to successfully conclude with a NSCIB certificate issued before 27 February 2026.
- For EUCC projects initiated between 27 February 2024 and 27 February 2025:
- Projects can be started through CBs and ITSEFs that are licensed for EUCC in the Netherlands, and are allowed to result in a EUCC certificate issued starting from 27 February 2025;
- In case of successful completion of the certification process before 27 February 2025, the NCCA will decide to formally approve the certificate issuance, provided the evaluation results are still valid on 27 February 2025. With this formal approval, the CB is positioned to issue the EUCC certificate on or shortly after 27 February 2025.
- From 27 February 2025 onwards;
- No NSCIB certification projects (including re-certification applications) can be initiated. Certification projects initiated before 27 February 2025 must result in a NSCIB certificate by 27 February 2026 at the latest;
- Maintenance on NSCIB certificates can only be requested and completed within two years of the initial certification date.
- From 27 February 2025 onwards, all Common Criteria certification projects will be EUCC projects, which can be initiated through CBs and ITSEFs licensed for EUCC in the Netherlands.
Frequently Asked Questions
Is it possible for my NSCIB project to result in an EUCC certificate?
Provided the NSCIB evaluation results are still valid, converting the project will require administrative effort and possibly extra evaluation and review steps. The CB should describe the extent of the reuse of NSCIB results in the assessment plan. For EUCC assurance level high, the EUCC certification process needs to be applied.
Is it possible for my EUCC project to result in a NSCIB certificate?
An EUCC project can, in addition to an EUCC certificate, result in a NSCIB certificate if the following conditions are met:
- There is a legitimate need for the NSCIB certificate;
- In addition to the EUCC application, an NSCIB application, including the argumentation why a NSCIB certificate is necessary, has been submitted and approved before 27 February 2025;
- The CB and ITSEF need to be licensed for both EUCC and NSCIB for the relevant scope;
- The EUCC certification process has successfully been concluded before 27 February 2026.
What are the practical implications of the statement “National CC schemes will cease to produce effects”?
The practical implications are described above. NSCIB will follow the SOG-IS policy on article 49 of the EUCC Implementing Regulation, possibly stricter. This SOG-IS policy provides interpretations of the Implementing Regulation regarding issuance of maintenance addendums, extension of the validity period or scope of certificates, etc.
The SOG-IS policy and the NSCIB transition restrictions as described above differentiate between certification projects and maintenance projects. Maintenance projects are not considered ‘certification projects’ as no new certificate is issued for the maintenance of existing certificates. From 27 February 2025 onwards, maintenance on NSCIB certificates can only be requested and completed within two years of the initial certification date, which is stricter than the SOG-IS policy.